Users might be vulnerable while accessing secure HTTPS websites, and their antivirus is to blame. A thorough research, conducted by experts at Mozilla Firefox, Google, Cloudflare and three American universities, shows that several popular antivirus software “drastically reduce connection security” and expose users to decryption attacks. This isn't new by any means and the HTTPS interception technique used by anti-viruses has been the subject of debate for several years.
Half of the world’s traffic is encrypted using the secure TCP/IP HTTPS protocol. Because traffic is encrypted, it’s not normally accessible for security inspections. However, antivirus products install their own root certificates on computers to be able to analyze HTTPS traffic. But instead of helping the user stay safe, this opens the gate to vulnerabilities, the study shows.
And here's the problem: Security software vendors are poorly handing inspection after the TLS handshake, according to the researchers. They’ve looked at eight billion TLS handshakes generated by Firefox, Chrome, Safari, and Internet Explorer, with antivirus software on. Researchers have analyzed Firefox’s update servers, a set of popular e-commerce websites and the Cloudflare content distribution network.
“In each case, we find more than an order of magnitude more interception than previously estimated,” the paper reads. They found interception happening on four percent of connections to Mozilla's Firefox update servers, 6.2 percent of e-commerce sites, and 10.9 percent of US Cloudflare connections. What’s worrying is that when intercepted, 97 percent of Firefox, 32 percent of e-commerce, and 54 percent of Cloudflare connections became less secure.
“As a class, interception products drastically reduce connection security. Most concernedly, 62% of traffic that traverses a network middlebox has reduced security and 58% of middlebox connections have severe vulnerabilities,” the report reads.
Not only do security software reduce connection security, but also introduce vulnerabilities such as failure to validate certificates.
“While the security community has long known that security products intercept connections, we have largely ignored the issue, believing that only a small fraction of connections are affected. However, we find that interception has become startlingly widespread and with worrying consequences,” the researchers say.
They’ve publish the result hoping to encourage manufacturers “to improve their security profiles and prompt the security community to discuss alternatives to HTTPS interception”.
Another serious problem enabled by the HTTPS scanning feature is that it breaks HTTP Public Key Pinning (HPKP).
HPKP is a technology enabling website operators to "remember" the public keys of SSL certificates in browsers, enforcing the use of specific public keys for specific websites. This reduces the risk of MiTM attacks using rogue/non authorized SSL certificates. But HTTPS scanning and HPKP can't work together, therefore if a website has HPKP enabled, when you access it the support for HPKP for that site will be disabled in the browser.
For the sake of example, we tested 3 antiviruses (Eset, Kaspersky and BitDefender) with HTTPS scanning feature enabled against a HPKP test website.
HPKP Test Results with HTTPS Scanning enabled:
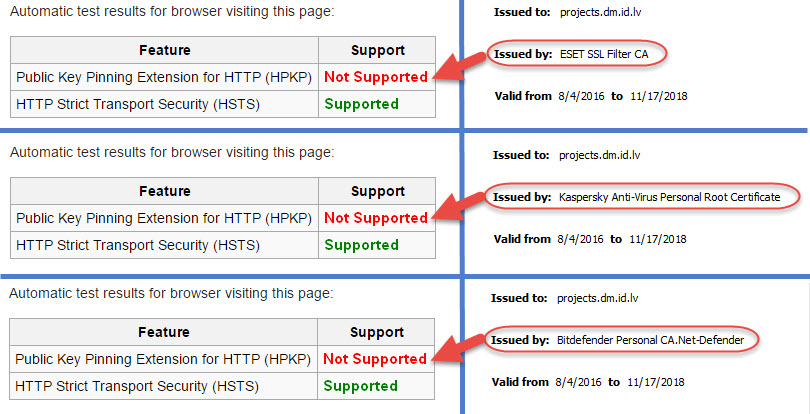
As you can see, the test shows Not Supported when the certificates are issued by the antiviruses.
HPKP Test Results with HTTPS Scanning disabled:
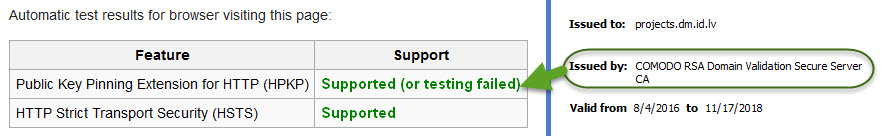
Now, with the HTTPS scanning disabled, the browser is using the correct certificate, issued by Comodo.
What to do
Meanwhile, our advice is to just disable the HTTPS scanning feature of your antivirus. This functionality contradicts the very idea of TLS/HTTPS point-to-point security and gives the users a false sense of security.
This is how to disable it in the 3 security products tested.
Eset Internet Security:
Setup > Internet Protection > Web Access Protection > Web Protocols > uncheck Enable HTTPS checking
Kaspersky Internet Security:
Settings > Additional > Network > Encrypted connections scanning > Do not scan encrypted connections
Note: By default it is scan encrypted connections upon request from security components which isn't so intrusive as with other products.
BitDefender Internet Security:
View Modules > Web Protection > disable Scan SSL
Further reading:
HTTPS Interception Weakens TLS Security
SSL/TLS/HTTPS: Keeping the public uninformed
HPKP: HTTP Public Key Pinning
Pinning hopes on pinning